Protect yourself against Phishing attempts
The last thing you want to hear is that money has been illegally removed from your bank account, or to find that your identity is being used to fraudulently obtain goods or services. In most cases this is the work of cybercriminals trying to get access to your personal information.
The security risk in an organisation is even greater. If you hand over your username and password to a cybercriminal, they could access information (marks, exams, personal data, etc.) that could be detrimental to individuals, to the department or to the university.
What is phishing?
Phishing is an attempt to get you to hand over personal, confidential information to a criminal. The requests may seem legitimate and may be perpetrated by phone, email or via the Internet. The danger lies in the fact that these phishing attempts look legitimate, sometimes even carrying an official-looking logo, and that they con you into providing information to fraudsters that you would not normally give to anyone else.
Phishing strategies
Cybercriminals use different methods to trick people, so it's wise to always be cautious. For example, you may get a phone call from a company saying that there is a virus on your computer and that you can pay them a fee to remove it and keep it clean thereafter.
Email is most commonly used as the route of attack, and will contain information that will make you take note of the email and react. It may say that your bank account or email account has been hacked and that you need to verify your details by sending them your username and password/PIN, or ask that you click on a link. Or they may try to fool you into thinking you're the latest millionaire in a sweepstake competition. You are then required to send them your banking details so that they can deposit the money into your bank account. These are common tell-tale signs of phishing attempts, so you need to be extra vigilant when you're asked to provide your personal information.
A legitimate company will never ask you to verify your account information, passwords, security questions, or other sensitive information. So, if you receive a suspicious email, delete it immediately.
Does UCT protect me from phishing?
No. ICTS provides protection from viruses and other malicious code by providing a desktop anti-virus program (McAfee EndPoint Security) and ensuring that regular patches are released via the network to protect your PC.
UCT cannot protect you from:
- Providing your information over the phone
- Completing an unsecured web form (phishing)
- Accessing malicious websites that harvest information/keystrokes from your computer
- Responding to false emails (phishing / spam)
When a malicious email (e.g. a phishing attempt) is reported and recognised, the UCT Computer Security Incident Response Team (CSIRT) will take all possible steps to minimise the risk to staff and students at UCT. However, we cannot guarantee total protection against such messages - hence it is your responsibility to be cautious and protect yourself from falling victim to such messages.
How do I protect myself against phishing?
Recognise legitimate emails
ICTS and the UCT CSIRT use a standard email template when sending out messages to staff and students at UCT. Recognising the template can help you to distinguish between legitimate messages from ICTS and phishing messages from fraudsters. Check your UCT mailbox for a recent message from ICTS and the UCT CSIRT to see an example of the templates used.
Protect your personal information
Don't give out personal information that may compromise you - whether this is by email, phone or online. Most major banks have publicly stated that they will NOT ask you to divulge confidential information over the phone or via email - unless you have phoned them to query or activate a service.
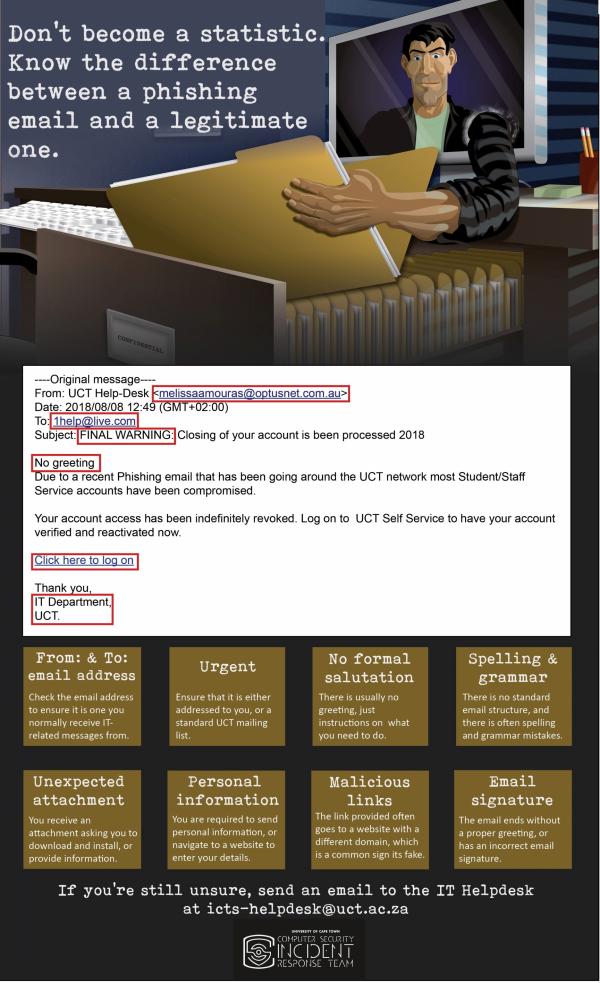
Analyse the details
If you are unsure about a message's authenticity, check the email header - which shows you the From, To, and Subject information. In most cases, there are either spelling mistakes, or the message isn't even from the company referred to in the email. View the infographic below to see an example of a recent phishing attack.
Phishing messages are often badly-written (using poor English) or the link provided is for a completely different website - which indicates that the legitimate company did not send you the message.
Look for signs
Websites that are not secure.
- They do not offer Secure Sockets Layer (SSL), a protocol developed for transmitting private documents via the Internet. (A secure website address will begin with https instead of http.)
- You do not see a closed lock symbol in your browser. (A closed lock indicates a secure site, while an open or absent lock indicates an unsecured site.) Any website where you are expected to exchange personal information (a banking site or an online store) should be secure.
- Websites that do not offer signed certificates. Security Certificates contain information about who it belongs to, who it was issued by, a unique serial number or other unique identification, valid dates and an encrypted "fingerprint" that can be used to verify the content of the certificate. If your browser warns you that the certificate can't be verified, be wary of the site.
- Websites that request information where the request is out of context with the action to be performed. For example, why do you need to supply your ID number or street address to read a document?
- Email messages supposedly sent to you by a bank, email provider or online store that ask you to provide personal information or click on a link in the email body.
- Email messages that seem to be IT-related, asking you to verify your account details or warning you of some dire consequence should you fail to comply, often contain a link that you have to click on to either log on or to provide sensitive information. For example, an email from "System admin" may claim that there has been a breach of security on your account and that the company needs you to submit personal information.
- Public computers at Internet cafes or other public spaces, where software may have been illegally installed to capture computer keystrokes.
- Pop-ups requesting personal information that appear once you gain access to a website that you trust.
- Pharming attempts - where a hacker redirects a legitimate website's traffic to a bogus site. Malware or a virus then takes over your web browser and when you try to access a legitimate website you'll be directed to a fake one. Once you provide your personal information on the site, hackers can access this information and fraudulently use it.
- Email attachments that you are not expecting.
- Telephone calls where the caller asks you to provide or verify personal information.
- Any emails claiming that there has been a breach of security on your account and they company needs you to submit personal information.
What to do if you suspect a phishing attempt or fall victim to one
- Report it
If you receive a suspicious email in your UCT mailbox asking you to click on a link, or requesting your personal information:
- DO NOT follow the message's instructions.
- DO NOT forward the message to anyone else.
Instead, report the attempt to the IT Helpdesk at icts-helpdesk@uct.ac.za and delete the message.
This reporting process applies only to your UCT email account. If you receive phishing attempts in non-UCT email accounts (e.g. Gmail), please follow the process specified by that email service provider. This can usually be found in the service provider's Help or Support pages and will help your service provider to minimise future phishing attempts to that email account.
- Change your password
If you responded to phishing attempt and handed over your password and username you need to immediately change your password immediately via Password Self-Service.
If you responded to a message requesting your username and password for external services (such as Facebook, LinkedIn, etc), log in to the relevant website and change your password immediately.
- Follow up with external service providers
If the phishing attempt relates to an external service provider - such as your bank:
- Contact the service provider and inform them that your account or information has been compromised.
- Let them know that someone has been impersonating their business (i.e. report the matter to them).
- Ask them to recommend the most secure methods to conduct your business with them. For example, many banks provide alternate accounts for online or telephone purchases. These special accounts limit the risk to a specific amount or transaction.