Information and cybersecurity attacks are now commonplace in all sectors. As cyberattacks become more advanced we want to ensure that you take all the necessary security measures while working and studying remotely to protect UCT and your digital assets, as well as the networks that you use.
We have created this web article to keep you updated on security risks and provide you with recommendations to stay protected.
Remember these security tips
While ICTS has put the necessary security measures in place to protect the UCT network, it is up to each of us to ensure that cybercriminals don’t gain unauthorised entry via one of our devices or home networks. Practice good cybersecurity hygiene by following our recommended security tips.
- Keep the operating system, applications, anti-virus and software that you use on your mobile devices and computer up-to-date. These are available via the applicable vendors’ websites. UCT-owned machines need to be connected to the UCT VPN to get the required operating system updates.
- Change any default login details and create a password that complies with UCT regulations.
- Back up your data regularly.
- Consider enabling a guest wireless network for untrusted devices.
- Enable wireless network encryption.
- Beware of phishing attacks by getting to know the tell-tale signs so that you can easily spot one sent via phone, SMS, instant message or phone.
Find out more what you can do to protect your home network by viewing our security guide.
Identified cyber attacks
October 2021
SMS pretending to be from senior UCT manager
September 2021
Security vulnerabilities with Netgear router
A Microsoft 365 Defender Research Team recently discovered security vulnerabilities with the NETGEAR DGN2200V1 router. The discovery was made while investigating capabilities for Microsoft Defender for Endpoint.
This particular router was launched in 2010 and is currently only used for ADSL internet connectivity.
The vulnerabilities, which were rated as-high-to-critical, were caused by an authentication bypass flaw. Attackers could easily access these routers and devices connected to it by adapting coding. These devices’ security information could then also be easily retrieved.
NETGEAR has since released patches to address these vulnerabilities.
This once again serves as a reminder to keep all devices and software updated by installing the latest updates and patches, which addresses potential security vulnerabilities.
August 2021
Beware of any requests to install or run unknown software on your devices
March 2021
Cybercriminals are now taking advantage of the fact that many sectors are continuing to allow their staff and students, where applicable, to work and study remotely.
The network address translation (NAT) slipstreaming attack is one such instance. Cybercriminals target home WiFi routers’ firewalls and network address translation (NAT), which modifies one IP address into another.
The way the attack works is that a cybercriminal tries to get you to visit a malicious website while you’re on your home network. These links are either sent via phishing emails or are hidden in online adverts. Once you’re on the website, the cybercriminal runs a script that fools your home router into divulging information about your device and those that are also connected to your home network. These devices are then all put at risk as cybercriminals can access and take control of it without the owners’ knowledge.
This is especially risky for devices that do not have security capabilities allowing them to be easily accessed and used to the cybercriminal’s advantage. So, if you’re using a mobile device or computer that doesn’t have anti-virus installed or hasn’t been updated and connect to the UCT network via your home router, this puts the university at risk.
What can I do to stay protected?
Google, Apple, Mozilla and Microsoft have released security patches for their respective web browsers, which are Chrome, Safari, Firefox and Edge.
We do, however, recommend that you ensure your home networks are secure to prevent it from becoming a target.
You can start by disabling the application-level gateway (ALG), which allows devices that use VoiP (Voice over IP) to communicate via the different IP addresses.
We have provided a general guide to disable ALG on your home router. For specific instructions for your device, please visit your vendor’s website.
TP-link Deco
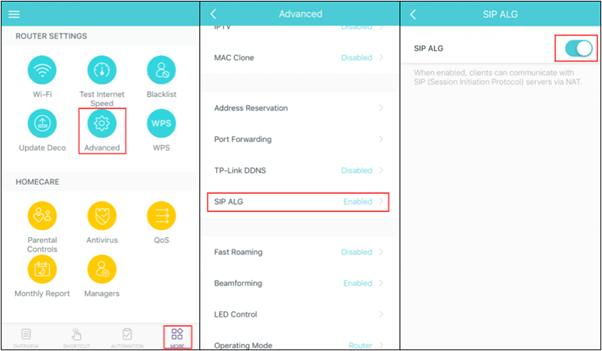
This option includes of a number of mini units that can be placed around your home to provide seamless WiFi and prevent any dead zones. For this option you need to disable SIP ALG via the Deco application.
Open the Deco App and click More > Advanced >SIP ALG to disable this option.
D-Link routers
These instructions can be applied to most WiFi routers.
- Open your web browser and enter http://dlinkrouter.local or http://192.168.0.1 in the address bar and press Enter on your keyboard.
- Enter your login details.
- On the D-Link landing page click the Features tab > Firewall.
- On the Firewall Settings page click Advanced Settings towards the bottom of the screen.
- Click SIP to disable SIP ALG. Click Save.
Additional resources
- https://www.armis.com/resources/iot-security-blog/nat-slipstreaming-v2-0-new-attack-variant-can-expose-all-internal-network-devices-to-the-internet/
- https://www.armis.com/resources/iot-security-blog/nat-slipstreaming-v2-0-new-attack-variant-can-expose-all-internal-network-devices-to-the-internet/#details
- https://samy.pl/slipstream/
- https://us-cert.cisa.gov/ncas/tips/ST15-002
