We laugh internally when we get a random phone call from Microsoft saying that there is a problem with our computer. While the consultant sounds very convincing, deep down we know it’s just another scam.
Sometimes, these calls come when you’re super stressed, which may lead you to do as you’re told to make the problem go away.
Imagine that you’re working frantically to complete a monthly report or an important assignment that’s due in a few hours. Adding to the pressure, you have people at home constantly walking in and talking to you. And the dog is barking because your neighbour just had to cut the grass at that time of day.
Your phone rings and you get the news that there is something wrong with your computer. Everything looks okay from your side, but the consultant keeps on going on saying that if you don’t install the software that can resolve the problem, your computer will crash. That means all your work will be gone, because you didn’t back up your document to the cloud. Your heart starts beating faster. Your palms get all sweaty.
You eventually give in and follow their instructions.
They then ask you for your credit card details to ensure you pay upfront. You give provide the info. Once they confirm payment, they install remote access software on your machine. All of a sudden, your computer switches off. The consultant says it’s normal. You breathe a sigh of relief.
A few seconds later, you hear a click on the phone line. There is no one on the other side. You call for them in vain. You try to call back, but don’t have a name or number. It then dawns on you: it was a scam.
Cybercriminals, fraudsters – whatever you want to call them – are constantly looking for opportunities to get their hands on your personal and banking information. That’s why you need to be on guard at all times.
These attacks come via phone, email, and instant message. If anything looks out of the ordinary, it probably is. If in doubt, contact the service provider directly by searching for their contact details online. Never use the details provided by the person who called you or sent you the message.
What if a reputable company phones and then asks me to verify my details?
There are times when your bank or mobile data provider will call about new offerings, or to follow up on an issue you’ve logged with them. If you’re uneasy about the call, rather politely end the call. If you want to discuss the offer or issue, call them back later – using the official number you find on the company’s website.
If you accept the offer, make sure you get the consultant’s name and a reference number. Most companies have a grace period in which you can cancel a contract. Before agreeing, make sure that you read the terms and conditions. If anything seems out of place, call back and ask for further assistance.
UCT Phish Bowl
To help you stay updated on the latest phishing attacks doing the rounds on campus, we have created a central location that you can check if the IT Helpdesk is aware of a suspicious email that you have received. The UCT Phish Bowl contains recent incidents as well as useful resources that you can use to prevent a phishing attack from happening to you.
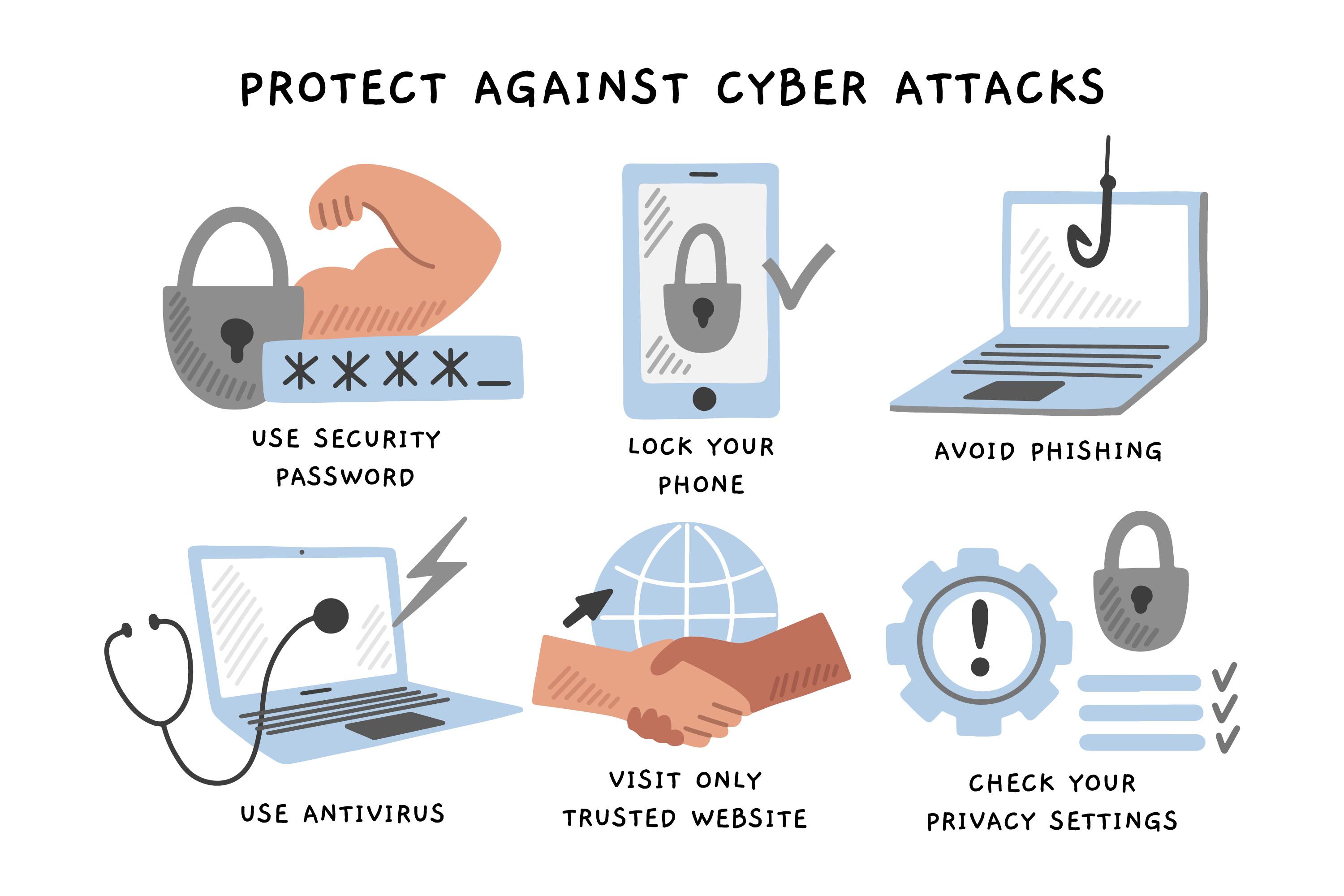
Remember, cybercriminals use all types of phishing tactics to access your personal information. Make sure you are aware of those telltale signs by checking out our tips below.
Tips
- Don't ever reply to emails, messages, or calls that request personal information – especially usernames and passwords.
- NEVER share your password or PIN with anyone – not even an ICTS representative, or representatives of your bank, mobile network, or other service providers.
- Ensure your passwords are complex by using a phrase, different languages or numbers, and symbols in place of letters.
- Ensure your anti-virus, operating system, software, and apps are always up to date.
- Do not open attachments unless you can verify the sender and the nature of the attachment.
- Don't open emails of unknown origin.
- Don't click on links in emails if you cannot recognise where the link directs you.
- Re-check links before clicking Search.
- Don't reply to spammers asking them to remove you from their mailing list. Replying just confirms your email address as valid, which encourages them to send you more spam.
- Please check the announcements on the ICTS and CSIRT websites for the latest alerts. If your suspicious email differs to the one in the announcement, please report it to the IT Helpdesk at icts-helpdesk@uct.ac.za. You can report any other cybersecurity issues to the CSIRT at csirt@uct.ac.za.
- Backup your data
- If something feels phishy, trust your gut and avoid the message or action.
